Is My Office or Home Being Bugged?
- Rick Herbert

- Feb 3
- 7 min read
Updated: Mar 3

In an era dominated by miniaturization and technological advancements in technical surveillance, the threat landscape has evolved to include tiny hidden listening devices, commonly known as (bugs) that pose significant privacy risks. Understanding the basics of their use and the availability of these hidden technical surveillance devices is crucial for safeguarding your personal and professional spaces from unwanted ears.
Formerly only associated with government spy agencies in the past, hidden technical surveillance devices can now be purchased online by members of the public and at very affordable prices and can be highly effective in gathering audio information discreetly. The covert placing of such devices requires little to no specialist training, just physical access to the intended targets location such as office, residential home, hotel room, or a physical mobile asset such as a motor vehicle, private yacht etc.
In this blog that I have compiled, we will solely focus on the specific threat of hidden audio listening devices (bugs). A threat in today's society which is much more common than you think.
Who Would Place a Hidden Audio Listening Device?
There are various reasons and types of individuals or entities who might place a hidden surveillance device in an office, home, vehicle, or other environment. In most cases the device will be purchased online and, in most cases, will be placed by the crass amateur.
Some common motivations and the potential perpetrators:
Competitors: Rival companies may seek to gain a competitive edge on the company by acquiring confidential business marketing strategies, product developments, revenue profits, or other sensitive information that will be of value to their organization.
Disgruntled Employees: Current or former employees with a grievance might use discreet technical surveillance to gather information for personal gain or to harm the company or a specific individual's reputation.
Personal Disputes: Individuals involved in personal disputes, such as divorces or custody battles, might hire private investigators with expertise in technical surveillance in order to gather evidence.
Insurance Investigations: Insurance companies might use technical surveillance to investigate fraudulent claims.
Exposure of Misconduct: Individuals seeking to expose corporate or governmental misconduct may use technical surveillance in order to gather evidence.
Harassment: Individuals with personal grudges or obsessions may use technical surveillance to monitor and harass their targets.
The Standard GSM Listening Device:

A GSM audio listening device (bug), example as shown above is a covert technical surveillance tool that uses the Global System for Mobile Communications (GSM) network to transmit audio speech from its target location to a remote listener. The listener can pretty much be anywhere in the world as long as they have a good network signal.
These devices are often used for eavesdropping or monitoring purposes and can be concealed in various objects such as power adapters, USB drives, smoke detectors, and other everyday items that you would find in an office and home environment.
How GSM Audio Listening Devices Work:
Sim Card Installation: Similar to a mobile phone, the device contains a slot for a SIM card, The SIM card enables the device to connect to the GSM network.
Activation: Once the SIM card is installed and the device is powered on, it can be activated either by calling its number or sending a specific SMS command.
Audio Transmission: When activated, the device captures audio from its surroundings using an in-built microphone. The audio is then transmitted over the GSM network to the listener's phone. Sound quality can vary dependent on the quality of the device and location where the device is placed.
Power Source: These devices can either be battery-powered or connected to an external power source. Battery-powered devices have the advantage of being portable and easy to conceal, while externally powered devices can operate continuously.
Control Commands: Many GSM listening devices allow the remote user to send SMS commands to control various functions, such as turning the microphone on or off, adjusting sensitivity, or receiving alerts when the device detects sound.
Radio Frequency (RF) Listening Device:
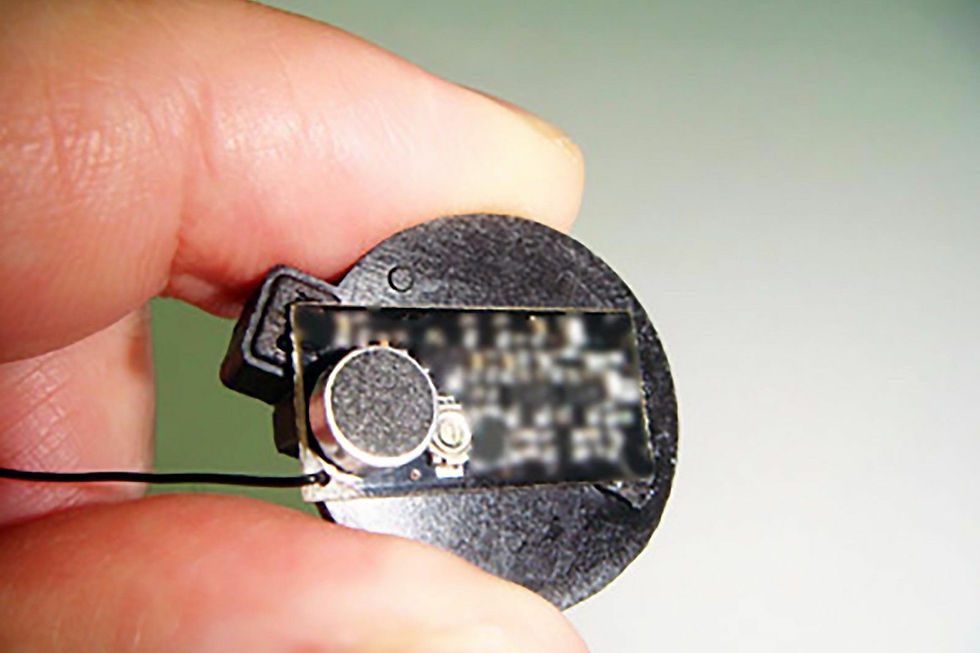
An RF (Radio Frequency) listening device is a type of covert technical surveillance tool that uses radio frequencies to transmit audio signals. These devices can be concealed in various objects to capture and relay conversations or sounds from a targeted area to a remote receiver.
Transmission Range: Some devices have limited range, ideal for use within a building or a specific room. Others can transmit over greater distances, useful for larger areas or outdoor environments.
Frequency Bands: VHF (Very High Frequency): Typically used for shorter distances. UHF (Ultra High Frequency): Offers longer range and better penetration through obstacles like walls.
Power Source: Battery Operated: Offers mobility but limited by battery life. Hard Wired: Can be concealed in objects that have a continuous electrical power supply, like lamps or smoke detectors, Light fittings.
Size and Concealment: These devices can be extremely small, allowing them to be hidden in everyday items such as pens, USB drives, or electrical outlets.
Audio Quality: Advanced models feature high-quality microphones and noise reduction technology to capture clear audio from the target area.
Detailed Visual & Physical Inspection to Detect Hidden Audio Listening Devices:

To search for hidden audio listening devices (bugs), you can use various methods and tools to detect and identify these hidden devices. It is vitally important prior to conducting a search which is commonly referred to as a (sweep) that you have a basic understanding of the various types of audio listening devices (bugs) available on the market and what they may look like, how they basically work and likely places where they might be covertly placed and concealed such as in the office environment, home, or other environment.

Here are some steps and strategies you can follow in order to carry out a sweep effectively and thoroughly if you suspect that you may be under some form of technical surveillance intrusion:
Gather Tools: Obtain the necessary tools required for the sweep as listed:
small powerful torch that can fit inside small spaces
screwdriver set
telescopic mirror set
large magnifying glass
RF detector
Smart phone to take photos of suspicious items.
Plan Sweep Inspection: Make a detailed checklist and a simple floor layout diagram of all areas and items to inspect:
include rooms that require sweeping
furniture
electronic items
common hiding spots
Affix coloured stickers to items during the pre-planning phase and which will help when conducting the sweep proper.
Prepare the Sweep Area: Turn off all electronic devices to minimize interference. Conduct the office environment sweep at a time when the area is least occupied to avoid drawing attention. Early mornings, late evenings, or scheduled maintenance times are ideal.
Double-Check High-Risk Areas:
conference rooms
around office desks
seating areas
rest rooms
next to land line telephones
outside employee smoking areas.
residential premises to include areas such as living room, kitchen, dining area, bathroom, bedrooms, electrical outlets, light fittings, land line phones, electronic items, decorative wall items and ornaments, kid's toys, plant pots, air vents, and thermostats to name a few.
motor vehicles to include areas such as under the seats and upholstery, dashboard, and around the steering column. Pay particular attention to unusual wires or components that don’t match the car's factory setup.

Check Common Hiding Spots:
examine ceiling light fixtures
lamps
under tables
smoke detectors
mobile phone chargers
WIFI routers
water dispensers
electrical outlets such as plug sockets
electrical extension leads
desk items such as pens
portable air fresheners
plant pots
picture frames
air vents & thermostats
removeable ceiling tiles
wall decorations
ornaments
mirrors.
Inspect Electronics: Turn off all electronics and listen for any unusual sounds that could indicate a recording device. Look at the following:
clocks
radios
televisions
other electronics for unusual wires or attached components.
Hardware computer keyloggers are usually easy to detect. Just look at the back of your computer and check for any unusual devices in your USB ports or connected to your keyboard cable. Just be sure that you aren't removing a legitimate USB adapter by mistake.
Look for Out-of-Place Items: Identify any new or unusual objects that seem out of place or have appeared recently. Be mindful of items that may be removed from site and returned at a later date by outside contractors.
Sweep the Room: Turn off all electronic devices and use an RF detector to scan the room. Move the detector slowly and methodically around the room, paying close attention to areas with electronic devices or wiring.
Check Specific Frequencies: Some audio listening devices often operate on radio frequencies. These devices will not contain a SIM card but may operate on a battery or be hard wired in to the electrical system. Make sure your detector covers a wide range of frequencies (1 MHz to 6 GHz).
Secure Your Network: Change your Wi-Fi passwords regularly and ensure your network is encrypted.
What to Do If You Find a Hidden Audio Listening Device:

Finding a hidden audio listening device can be unsettling and raise significant concerns about your privacy and security. Here are steps you should take if you discover such a device:
Preserve Evidence: Avoid touching or tampering with the device to preserve potential evidence. This will help law enforcement, or investigators determine the origin and purpose of the device found.
Document the Discovery: Take detailed notes and photographs of the device in its found location. Include the date, time, and any identifying details.
Prevent Data Transmission: Turn off electronic devices and Wi-Fi to prevent any potential data from being transmitted while you assess the situation.
Contact Law Enforcement: Report the discovery to local law enforcement authorities. Provide them with all the documentation and evidence you have collected.
Consult Legal Counsel: Depending on your jurisdiction, consult a lawyer to understand your rights and any legal steps you should take.
Check for More Devices: Manually inspect other areas and objects in your environment that might conceal additional devices.
Conduct Regular Sweeps: Conduct regular physical and electronic sweeps of your environment to detect and prevent future surveillance attempts.
Educate and Train: Educate employees or household members about the importance of physical security and how to recognize and deal with potential technical surveillance threats.
Conclusion:
Eavesdropping by the use of hidden audio listening devices is indeed more common today than you think due to technological advancements, the proliferation of digital communications, and the increasing ease of access to surveillance tools from reputable online suppliers. This trend underscores the importance of being vigilant about privacy and security, whether in personal, corporate, or governmental contexts. Implementing robust security measures, staying informed about potential threats, and understanding the legal implications of surveillance can help mitigate the risks associated with eavesdropping.
Please feel free to contact me should you have any queries or concerns related to technical surveillance threats.
Rick Herbert
Security Consultant
Gibraltar



_edited.jpg)

Komentar